2018
A Software Defined Network-Based Security Assessment Framework for CloudIoT
Student:Zhuobing Han Supervisor:Xiaohong Li
This article is published at journey《IEEE Internet of Things Journal》(Volume:5,Issue:3,June 2018 )(《IEEE IoTJ》).
Abstract:
We develop an end-to-end security assessment framework based on software defined network (SDN) to evaluate the security level for the given CloudIoT offering. Specially, in order to simplify the network controls and focus on the analysis about the data flow through CloudIoT, we develop a three-layer framework by integrating SDN and CloudIoT, which consists of 23 different indicators to describe its security features. Then, the interviews from industry and academic are carried out to understand the importance of these features for the overall security.
An efficient approach for verifying automobile distributed application systems on timing property
Student:[Cooperated] Supervisor:Xiaohong Li
This article is published at International Conference on Software Engineering(ICSE).
Abstract
The applications are in charge of realizing functions and often interact with each other via the communication protocol such as controller area network (CAN). There are two complex execution characteristics in the OSEK/VDX vehicle-mounted systems: (i) tasks within an application concurrently execute on a processor under the scheduling of OSEK/VDX OS; (ii) applications simultaneously run on the different processors and communicate each other sometimes.
DeepWeak: Reasoning Common Software Weaknesses via Knowledge Graph Embedding
Student:Zhuobing Han Supervisor:Xiaohong Li
This article is published at International Conference on Software Analysis ,Evolution,and Reengineering(SNAER).
Abstract
The first to investigate the knowledge graph representation of common software weaknesses and the reasoning tasks on this knowledge graph. Propose a knowledge graph embedding approach to embed the structural and textual knowledge of CWEs into vector representations. Conduct extensive experiments to evaluate the effectiveness of knowledge graph embeddings in reasoning over relations and common consequences of CWEs.
SCC-rFMQ learning in Cooperative Markov Games with Continuous Actions
Student:Chengwei Zhang Supervisor:Xiaohong Li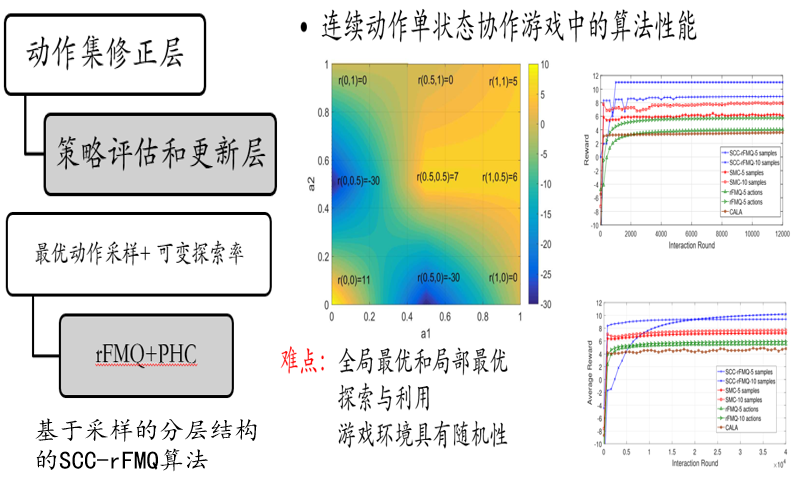
This article is published at International Conference on Autonomous Agents and Multiagent Systems (AAMAS 2018).
Abstract
We propose an independent learner hierarchical method SCC-rFMQ which can handle coordination problems in continuous action cooperative Markov games effectively.
2017
Loopster: Static Loop Termination Analysis
Student:Xiaofei Xie Supervisor:Xiaohong Li
This article is published at IEEE Transactions on Software Engineering, 2017.
Abstract
In this paper, we propose a novel approach, which performs an efficient static analysis to decide the termination. It adopts a divide-and-conquer approach: (1) extract individual paths from a target multi-path loop and analyze the termination of each path, (2) analyze the dependencies between each two paths, and then (3) determine the overall termination of the target loop based on the relations among paths..
A Service-Based Approach to Situational Correlation and Analyses of Stream Sensor Data
Student:Zhongmei Zhang Supervisor:Xiaohong Li
The paper is published at 2017 IEEE International Conference on Web Services(ICWS 2017).
Abstract:
In this paper, we propose a deep learning approach to predict multi-class severity level of software vulnerability using only vulnerability description. Instead of relying on manual feature engineering, our approach uses word embeddings and a one-layer shallow Convolutional Neural Network (CNN) to automatically capture discriminative word and sentence features of vulnerability descriptions for predicting vulnerability severity. We exploit large amounts of vulnerability data from the Common Vulnerabilities and Exposures (CVE) database to train and test our approach.
Optimal Personalized Defense Strategy Against Man-In-The-Middle Attack
Student:Shuxin Li Supervisor:Xiaohong Li
The paper is published at Proceedings of the 31st AAAI Conference on Artificial Intelligence (AAAI'17).
Abstract:
This paper proposes a game-theoretic optimal personalized defense strategy from a different perspective, which aims at minimizing the loss that the whole system sustains given that the MITM attacks are inevitable. We model the interaction between the attacker and the defender as a Stackelberg security game and adopt the Strong Stackelberg Equilibrium (SSE) as the defender’s optimal defense strategy. Since the defender’s strategy space is infinite in our model, we employ a novel method to reduce the searching space of computing the optimal defense strategy. The results indicate that our game-theoretic defense strategy significantly outperforms other non-strategic defense strategies in terms of decreasing the total losses against MITM attacks.
Defending Against Man-In-The-Middle Attack in Repeated Games
Student:Shuxin Li Supervisor:Xiaohong Li
This article is published at International Joint Conference on Artificial Intelligence(IJCAI'17).
Abstract
We solve the MITM attack-defense problem under a repeated simultaneous-move game model aiming at minimizing the defenders’ own loss. Nash equilibrium is adopted as the optimal defense strategy for the defenders. We also provide theoretical analysis of the uniqueness of Nash equilibrium which addresses the equilibrium selection problem. We propose learning algorithms for the defenders and the attacker to learn towards the Nash equilibrium. Simulation results show that our learning algorithm can converge to Nash equilibrium efficiently.
2016
Computing Disjunctive Loop Summary via Path Dependency Analysis
Student:Xiaofei Xie Supervisor:Xiaohong Li
The paper is published at International Symposium on the Foundations of Software Engineering (FSE),and receive ACM SIGSOFT Distinguished Paper Award.
Abstract:
Loops are challenging structures for program analysis, especially when loops contain multiple paths with complex interleaving executions among these paths. In this paper, we first propose a classification of multi-path loops to understand the complexity of the loop execution, which is based on the variable updates on the loop conditions and the execution order of the loop paths. Secondly, we propose a loop analysis framework, named Proteus, which takes a loop program and a set of variables of interest as inputs and summarizes path-sensitive loop effects on the variables. The key contribution is to use a path dependency automaton (PDA) to capture the execution dependency between the paths. A DFS-based algorithm is proposed to traverse the PDA to summarize the effect for all feasible executions in the loop. The experimental results show that Proteus is effective in three applications: Proteus can 1) compute a more precise bound than the existing loop bound analysis techniques; 2) significantly outperform state-of-the-art tools for loop verification; and 3) generate test cases for deep loops within one second, while KLEE and Pex either need much more time or fail.
S-looper: automatic summarization for multipath string loops
Student:Xiaofei Xie Supervisor:Xiaohong Li
The paper is published at 2015 International Symposium on Software Testing and Analysis.
In this paper, we propose an approach, named S-Looper, to automatically summarize a type of loops related to a string traversal. This type of loops can contain multiple paths, and the branch conditions in the loop can be related to string content. Our approach is to identify patterns of the string based on the branch conditions along each path in the loop. Based on such patterns, we then generate a loop summary that describes the path conditions of a loop traversal as well as the symbolic values of each variable at the exit of a loop. Combined with vulnerability conditions, we are thus able to generate test inputs that traverse a loop in a specific way and lead to exploitation.
Socially-aware Multiagent Learning towards Socially Optimal Outcomes
Student:Chengwei Zhang Supervisor:Xiaohong Li
The paper is published at Proceedings of ECAI2016(CCF B).
Abstract:
Motivation: In multi-agent environments, it is desirable if the agents can learn to coordinate towards socially optimal outcomes, while also avoiding being exploited by selfish opponents.
Contribution: propose a novel gradient ascent based algorithm (SA-IGA) which augments the basic gradient-ascent algorithm by incorporating social awareness into the policy update process.
